A Review Of 100% Guarantee 1Z0-821 Practice Question
Certleader offers free demo for 1Z0-821 exam. "Oracle Solaris 11 System Administrator", also known as 1Z0-821 exam, is a Oracle Certification. This set of posts, Passing the Oracle 1Z0-821 exam, will help you answer those questions. The 1Z0-821 Questions & Answers covers all the knowledge points of the real exam. 100% real Oracle 1Z0-821 exams and revised by experts!
Online Oracle 1Z0-821 free dumps demo Below:
NEW QUESTION 1
A change in your company’s security policy now requires an audit trial of all administrators assuming the sysadm role, capturing:
There are two command necessary to accomplish this change. One is a rolemod command. What is the other?
- A. auditconfig set policy=argv
- B. auditconfig -setpolicy +argv
- C. auditconfig -setflags lo, ex sysadm
- D. auditconfig set flags=lo, ex sysadm
Answer: B
Explanation:
Audit Significant Events in Addition to Login/Logout (see step 2 below)
Use this procedure to audit administrative commands, attempts to invade the system, and other significant events as specified by your site security policy.
For all users and roles, add the AUE_PFEXEC audit event to their preselection mask.
# usermod -K audit_flags=lo, ps:no username
# rolemod -K audit_flags=lo, ps:no rolename
# auditconfig -setpolicy +argv
3- Record the environment in which audited commands are executed.
# auditconfig -setpolicy +arge
Note: [-t] -setpolicy [+|-]policy_flag[, policy_flag ...]
Set the kernel audit policy. A policy policy_flag is literal strings that denotes an audit policy. A prefix of + adds the policies specified to the current audit policies. A prefix of - removes the policies specified from the current audit policies. No policies can be set from a local zone unless the perzone policy is first set from the global zone.
NEW QUESTION 2
alice is a user account used by Alice on a Solaris 11 system. sadmin is a role account on the same system.
Your task is to add the command /usr/sbin/cryptoadm to the Network management profile, so that Alice can execute it, while assuming the sadmin role.
Select the three activities necessary to accomplish this.
- A. To the file /etc/security/prof_attr, add the line: Network Management: solaris:cmd:RO::/usr/sbin/cryptoadm:euid=0
- B. To the file /etc/security/auth_attr, add the line:Network Management:solaris:cmd:RO::/usr/sbin/cryptoadm:euid=0
- C. To the file /etc/security/exec_attr.d/local-entriies, add the line:Network Management: solaris:cmd:RO::/usr/sbin/cryptoadm:euid=0
- D. Run the roles alice to ensure that alice may assume the role sadmin.
- E. Run the command profiles sadmin to ensure that the role sadmin includes the network Management profile.
- F. Run the command profiles alice to ensure that the Alice has permissions to access the Network management profile.
- G. Run the command profiles “Network management” to ensure that the Network management profile includes the sadmin role.
Answer: CDG
Explanation:
C: /etc/security/exec_attr is a local database that specifies the execution attributes associated with profiles. The exec_attr file can be used with other sources for execution profiles, including the exec_attr NIS map and NIS+ table.
A profile is a logical grouping of authorizations and commands that is interpreted by a profile shell to form a secure execution environment.
NEW QUESTION 3
To confirm the IP addresses and netmasks have been correctly configured on the network interfaces, which command(s) should you use?
- A. ipadm show-if
- B. ipadm show-nic
- C. ipadm show-addr
- D. ipadm show-addripadm show-mask
- E. ipadm show-ipipadm show-mask
- F. ipadm show-config
Answer: C
Explanation:
Show address information, either for the given addrobj or all the address objects configured on the specified interface, including the address objects that are only in the persistent configuration.
Example:
# ipadm show-addr
ADDROBJ TYPE STATE ADDR
lo0/v4 static ok 127.0.0.1/8 lo0/v6 static ok ::1/128
NEW QUESTION 4
The ZFS configuration on your server is:
Pool1 6.67G31K/pool Pool1/data31K31K/data
Select the three commands that you would use to 1. Create, 2. List, and 3. Delete a snapshot of the /data file system.
- A. zfs snapshot pool1/data@now
- B. zfs create snapshot pool1/data@now
- C. zfs list -t snapshot
- D. zfs list -t snapshot pool1/data
- E. zfs destroy pool1/data@now
- F. zfs destroy snapshot pool1/data@now
Answer: ADE
Explanation:
A: Snapshots are created by using the zfs snapshot command, which takes as its only argument the name of the snapshot to create.
D: You can list snapshots as follows:
# zfs list -t snapshot
E: Snapshots are destroyed by using the zfs destroy command. For example:
# zfs destroy tank/home/ahrens@now
NEW QUESTION 5
You are logged in as root to a newly installed Solaris 11 system. You issue the command useradd -d, and then examine the /usr/sadm/defadduser file. This file includes the entry defshell=/bin/sh. Which shell will now be the default for the next account created?
- A. bash shell
- B. C shell
- C. korn shod
- D. bourne shell
Answer: A
Explanation:
Oracle Solaris 11 introduces user environment and command-line argument changes that include the following:
* Shell changes - The default shell, /bin/sh, is now linked to ksh93. The default user shell is the Bourne-again (bash) shell.
* The legacy Bourne shell is available as /usr/sunos/bin/sh.
* The legacy ksh88 is available as /usr/sunos/bin/ksh from the shell/ksh88 package.
* Korn shell compatibility information is available in /usr/share/doc/ksh/COMPATIBILITY.
NEW QUESTION 6
You have edited /etc/profile to include the lines: dennis_says=hello
export dennie_says
You have also edited /etc/skel/local.profile to include the line: dennis_says=world
You now create a new user account brian, and specify use of the bash shell. When brian logs in and enters
Echo $dennis_says
What will he see, and why?
- A. world, because the local.profile entry will be executed last
- B. hello, because the global /etc/profile entry overrides the local.profile entry
- C. hello, because the local.profile entry is not automatically sourced on login
- D. hello, because the value specified in local.profile was not exported
- E. nothing, because the variable was not exported in local.profile
Answer: A
Explanation:
The $HOME/.profile file is an initialization file that is executed after the /etc/profile when logging in to the Bourne or Korn shell. The file contains user preferences for variable settings. If the ENV variable is set to .kshrc, the .kshrc file executes every time a new shell
begins execution. The $HOME/.profile is copied from the /etc/skel/local.profile file by the Administration Tool when creating a new account.
Note: /etc/skel/local.profile
Per-system configuration file for sh/ksh/ksh93/bash login sessions, installed for new users
NEW QUESTION 7
You are troubleshooting a newly installed desktop Oracle Solaris 11 system with a single network interface. From this system, you can connect to other systems within the company
intranet, but cannot access any external services (such as websites and email), even when using IP addresses.
Examining the routing table confirms that the default route to 192.168.1.1 is missing. DHCP is not used at this site. Which two commands will temporarily mid permanently configure the default route?
- A. ipadm set-gateway 192.168.1.1
- B. route add default 192.168.1.1
- C. ipadm set-default 192.168.1.1
- D. dladm route-add –d 192.168.1.1
- E. echo 192.168.1.1 >/etc/gateway
- F. echo 192.168.1.1 >/etc/defaultrouter
Answer: BF
Explanation:
B: Setting the default route on Solaris is easy. If you are trying to just set the route temporarily you can use the route command:
Route add default <ipaddress> Example:
Route add default 192.168.1.1
Note: Route command manipulates the kernel routing tables. Routing is the process of forwarding a packet from one computer to another. It is based on the IP address in the IP packet header and netmask.
F: If you want the route to be persisted when you reboot the system, you will need to set the route in the /etc/defaultrouter file.
/etc/defaultrouter Example:
Echo 192.168.1.1 > /etc/defaultrouter
NEW QUESTION 8
zone1 is a non-global zone that has been configured and installed.
zone1 was taken down for maintenance, and the following command was run: zoneadm -z zone1 mark incomplete
The following information is displayed when listing the zones on your system:
Which task needs to be performed before you can boot zone1?
- A. The zone needs to be installed.
- B. The zone needs to be brought to the ready state.
- C. The zone needs to be uninstalled and reinstalled.
- D. The zone needs to be brought to the complete state.
Answer: C
Explanation:
If administrative changes on the system have rendered a zone unusable or inconsistent, it is possible to change the state of an installed zone to incomplete.
Marking a zone incomplete is irreversible. The only action that can be taken on a zone marked incomplete is to uninstall the zone and return it to the configured state.
NEW QUESTION 9
You are troubleshooting the Oracle Solaris11 Automated Installer (AI), which is not connecting with the IPS software repository.
Which three steps will help determine the cause of DNS name resolution failure?
- A. Verify the contents of /etc/resolve.conf.
- B. Run netstat -nr to verify the routing to the DNS server.
- C. Ping the IP address of the IPS server to verify connectivity.
- D. On the installation server, verify that the menu.1st file for the client points to a valid boot arc hive.
- E. Run df -k to verify that the boot directory containing the boot archive is loopback mounted under /etc/netboot.
- F. Run the command /sbin/dhcpinfo DNSserv to ensure that the DHCP server providing the DNS server information.
Answer: ABF
Explanation:
Check DNS
* (A) Check whether DNS is configured on your client by verifying that a non-empty
/etc/resolv.conf file exists.
* (F) If /etc/resolv.conf does not exist or is empty, check that your DHCP server is providing DNS server information to the client:
# /sbin/dhcpinfo DNSserv
If this command returns nothing, the DHCP server is not set up to provide DNS server information to the client. Contact your DHCP administrator to correct this problem.
* (B) If an /etc/resolv.conf file exists and is properly configured, check for the following possible problems and contact your system administrator for resolution:
** The DNS server might not be resolving your IPS repository server name.
** No default route to reach the DNS server exists.
NEW QUESTION 10
In a default standalone installation of Oracle Solaris 11, what is the default minimum length in characters of a user password, and where is the minimum password length defined?
- A. Default minimum length is 8, and is defined in /etc/default/password.
- B. Default minimum length is 6, and is defined in /etc/default/password.
- C. Default minimum length is 8, and is defined in /etc/shadow.
- D. Default minimum length is 6, and is defined in /etc/shadow.
- E. Default minimum length is 8, and is defined in /usr/sadm/defadduser.
- F. Default minimum length is 6, and is defined in /usr/sadm/defadduser.
Answer: B
Explanation:
By default, the passwd command assumes a minimum length of six characters. You can use the PASSLENGTH default in the /etc/defaults/passwd files to change that by setting the minimum number of characters that a user's password must contain to some other number.
NEW QUESTION 11
The interface net3 should be operating, but is not. Command:
Which command should you enter next?
- A. ipadm create-ip
- B. ipadm enable-if
- C. ipadm show-if
- D. ipadm up-addr
Answer: B
Explanation:
Enable-if -t interface
Enables the given interface by reading the configuration from the persistent store. All the persistent interface properties, if any, are applied and all the persistent addresses, if any, on the given interface will be enabled.
-t, --temporary
Specifies that the enable is temporary and changes apply only to the active configuration.
NEW QUESTION 12
You want to delete the IPv4 address on the interface net3. Which command should you use?
- A. ipadm delete-ip net3/v4
- B. ipadm down-addr net3/v4
- C. ipadm disable-if net3/v4
- D. ipadm delete-vni net3/v4
- E. ipadm delete-addr net3/v4
- F. ipadm deiete-ipv4 ner3/v4
Answer: E
Explanation:
The ipadm delete-addr subcommand removes addresses from interfaces. To remove an address from the IPMP group, type the following command:
# ipadm delete-addr addrobj
The addrobj uses the naming convention inder-interface/user-string.
NEW QUESTION 13
You are having an issue with the shutdown command. You wish to determine if the file is a script or an executable program. Which command would you use to determine this?
- A. od shutdown
- B. file shutdown
- C. test shutdown
- D. cksum shutdown
- E. attrib shutdown
Answer: B
Explanation:
The file command determines the file type file tests each argument in an attempt to classify it. There are three sets of tests, performed in this order: filesystem tests, magic tests, and language tests. The first test that succeeds causes the file type to be printed.
NEW QUESTION 14
You log in to the system as user1, then switch user to root by using the su - command. After entering the correct password, yon enter the following commands:
whoami;who am i;id
Which option correctly represents the output?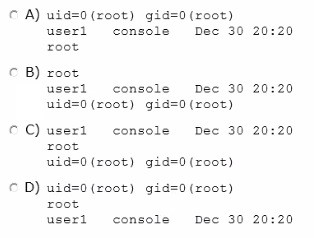
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer: B
Explanation:
* The whoami utility displays your effective user ID as a name. Here this would be root.
* who am i
The command who shows who is logged on. Here this would be:
user1 console Dec 30 20:20
* The id utility displays the user and group names and numeric IDs, of the calling process, to the standard output. If the real and effective IDs are different, both are displayed, otherwise only the real ID is displayed.
Here this would be: uid=0(root) gid=0(root)
Note:
Each UNIX proces has 3 UIDs associated to it. Superuser privilege is UID=0.
Real UID
--------
This is the UID of the user/process that created THIS process. It can be changed only if the running process has EUID=0.
Effective UID
-------------
This UID is used to evaluate privileges of the process to perform a particular action. EUID can be change either to RUID, or SUID if EUID!=0. If EUID=0, it can be changed to anything.
Saved UID
---------
If the binary image file, that was launched has a Set-UID bit on, SUID will be the UID of the owner of the file. Otherwise, SUID will be the RUID.
NEW QUESTION 15
User1 is attempting to run the following command: cp bigfile verybig
The system displays the following errer:
cp: cannot create verybig: Disc quota exceeded
Your initial troubleshooting shows that the df -h command indicates the account is at 100% capacity. What command would you use to determine how much disk space the user has available?
- A. zfs get quota rpool/export/home/user1
- B. zfs userused@user1
- C. zfs quota=1M /rpool/export/home/user1
- D. df –h | grep user1
Answer: A
Explanation:
ZFS quotas can be set and displayed by using the zfs set and zfs get commands. In the following example, a quota of 10 Gbytes is set on tank/home/bonwick.
# zfs set quota=10G tank/home/bonwick
# zfs get quota tank/home/bonwick NAME PROPERTY VALUE SOURCE
tank/home/bonwick quota 10.0G local
NEW QUESTION 16
Identify the two security features incorporated in the Oracle Solaris 11 Cryptographic Framework.
- A. Layer 5 IP address encryptions
- B. Internet protocol security
- C. Diffie-Kerberos coaxial key encryption
- D. Signed cryptographic plugins (providers)
- E. Kernel support for signed antivirus plugins
Answer: DE
Explanation:
The framework enables providers of cryptographic services to have their services used by many consumers in the Oracle Solaris operating system. Another name for providers is plugins. The framework allows three types of plugins:
* User-level plugins - Shared objects that provide services by using PKCS #11 libraries, such as pkcs11_softtoken.so.1.
* Kernel-level plugins - Kernel modules that provide implementations of cryptographic algorithms in software, such as AES.
Many of the algorithms in the framework are optimized for x86 with the SSE2 instruction set and for SPARC hardware.
* Hardware plugins - Device drivers and their associated hardware accelerators. The Niagara chips, the ncp and n2cp device drivers, are one example. A hardware accelerator offloads expensive cryptographic functions from the operating system. The Sun Crypto Accelerator 6000 board is one example.
NEW QUESTION 17
Which five statements describe options available for installing the Oracle Solaris 11operating system using the installation media?
- A. You can perform a text or LiveCD installation locally or over the network.
- B. The text Installer does not install the GNOME deskto
- C. The GNOME desktop package must he added after you have installed the operating system.
- D. The LiveCD Installation cannot be used to install multiple instances of Oracle Solaris.
- E. The LiveCD installer cannot be used if you need to preserve a specific Solaris Volume Table of Contents (VTOC) slice in your current operating system.
- F. The LiveCD Installer is for x86 platforms only.
- G. The GUI installer cannot be used to upgrade your operating system from Solaris 10.
- H. If you are installing Oracle Solaris 11 on an x86-based system that will have more than one operating system installed in it, you cannot partition your disk during the installation process.
- I. The LiveCD installer can be used for SPARC or x86 platforms.
Answer: ABDFH
Explanation:
A: If the network is setup to perform automated installations, you can perform a text installation over the network by setting up an install service on the network and selecting a text installation when the client system boots.
B: After a fresh install of Solaris 11 express, only the console mode is activated. To add Gnome, simply do :
$ sudo pkg install slim_install
This will install additional packages that are not installed by default. D: The text installer advantages over the GUI installer include:
* In addition to modifying partitions, the text installer enables you to create and modify VTOC slices within the Solaris partition.
F: How do I upgrade my Solaris 10 or lower systems to Solaris 11?
Unfortunately, you CAN'T. There is no direct upgrade installer or other tool that will allow you to upgrade from earlier releases of Solaris to Solaris 11. This is primarily due to the vast changes in the packaging mechanism in Solaris 10.
NEW QUESTION 18
Which network protocol provides connectionless, packet-oriented communication between applications?
- A. TCP
- B. UDP
- C. IP
- D. ICMP
- E. NFS
- F. IPSec
Answer: B
Explanation:
The User Datagram Protocol (UDP) is one of the core members of the Internet Protocol Suite, the set of network protocols used for the Internet. With UDP, computer applications can send messages, in this case referred to as datagrams, to other hosts on an Internet Protocol (IP) network without requiring prior communications to set up special transmission channels or data paths.
Compared to TCP, UDP is a simpler message-based connectionless protocol.
NEW QUESTION 19
You display the IP interface information with ipmpstat -i.
Which two characteristics are indicated by characters that may be included in the FLAGS column?
- A. default route
- B. IP forwarding enabled IS
- C. allocated to global zone
- D. unusable due to being inactive
- E. nominated to send/receive IPv4 multicast for its IPMP group
Answer: DE
Explanation:
FLAGS
Indicates the status of each underlying interface, which can be one or any combination of the following:
(D) d indicates that the interface is down and therefore unusable.
(E) M indicates that the interface is designated by the system to send and receive IPv6 multicast traffic for the IPMP group.
Note:
i indicates that the INACTIVE flag is set for the interface. Therefore, the interface is not used to send or receive data traffic.
s indicates that the interface is configured to be a standby interface.
m indicates that the interface is designated by the system to send and receive IPv4 multicast traffic for the IPMP group.
b indicates that the interface is designated by the system to receive broadcast traffic for the IPMP group.
h indicates that the interface shares a duplicate physical hardware address with another interface and has been taken offline. The h flag indicates that the interface is unusable.
NEW QUESTION 20
On server A, you enter the following command to add a static route to serverA route -p add
-host 192.168.1.101 192.168.1.101 -static
What is the purpose of this command?
- A. to temporarily bypass IP Filter rules
- B. to specify an IPMP target IP address to in.mpathd
- C. to specify routing to an adjacent network when in.rdisc is not used
- D. to specify routing to an adjacent network when in.routed is not used
- E. to ensure the IP address for serverB is not flushed from the ARP cache
- F. to optimize link aggregation using a direct connection between two systems
Answer: B
Explanation:
Note: # route -p add -host destination-IP gateway-IP -static
where destination-IP and gateway-IP are IPv4 addresses of the host to be used as a target.
For example, you would type the following to specify the target system 192.168.10.137, which is on the same subnet as the interfaces in IPMP group itops0:
$ route -p add -host 192.168.10.137 192.168.10.137 -static
This new route will be automatically configured every time the system is restarted. If you
want to define only a temporary route to a target system for probe-based failure detection, then do not use the -p option.
NEW QUESTION 21
Which three options accurately describe Oracle Solaris 11 zones?
- A. can be NFS servers
- B. are whole root type only
- C. cannot have their own time zone setting
- D. can execute z£s and zpool commands (from a non-global zone)
- E. are virtualized operating system environments, each with its own dedicated OS and kernel
- F. are virtualized operating system environments, created with a single instance of the OS shared kernel
Answer: ADF
Explanation:
A: Zones can use Oracle Solaris 11 products and features such as the following: Oracle Solaris ZFS encryption
Network virtualization and QoS CIFS and NFS
C: Non-global zones cannot modify the system clock by default, but each zone can have a separate time zone setting.
F (not E): The Oracle Solaris Zones partitioning technology is used to virtualize operating system services and provide an isolated and secure environment for running applications. A zone is a virtualized operating system environment created within a single instance of the Oracle Solaris operating system.
NEW QUESTION 22
......
P.S. Easily pass 1Z0-821 Exam with 243 Q&As Certleader Dumps & pdf Version, Welcome to Download the Newest Certleader 1Z0-821 Dumps: https://www.certleader.com/1Z0-821-dumps.html (243 New Questions)